Can you imagine a world where every device is interconnected, allowing seamless control and monitoring from anywhere? Achieving this vision is not only possible but increasingly essential in today's hyper-connected landscape. As the Internet of Things (IoT) continues to expand, remote monitoring solutions like SSH have emerged as indispensable tools for managing devices securely and efficiently. Whether you're an engineer, hobbyist, or tech enthusiast, understanding how SSH can be leveraged with platforms like Raspberry Pi and Ubuntu opens up endless possibilities for innovation.
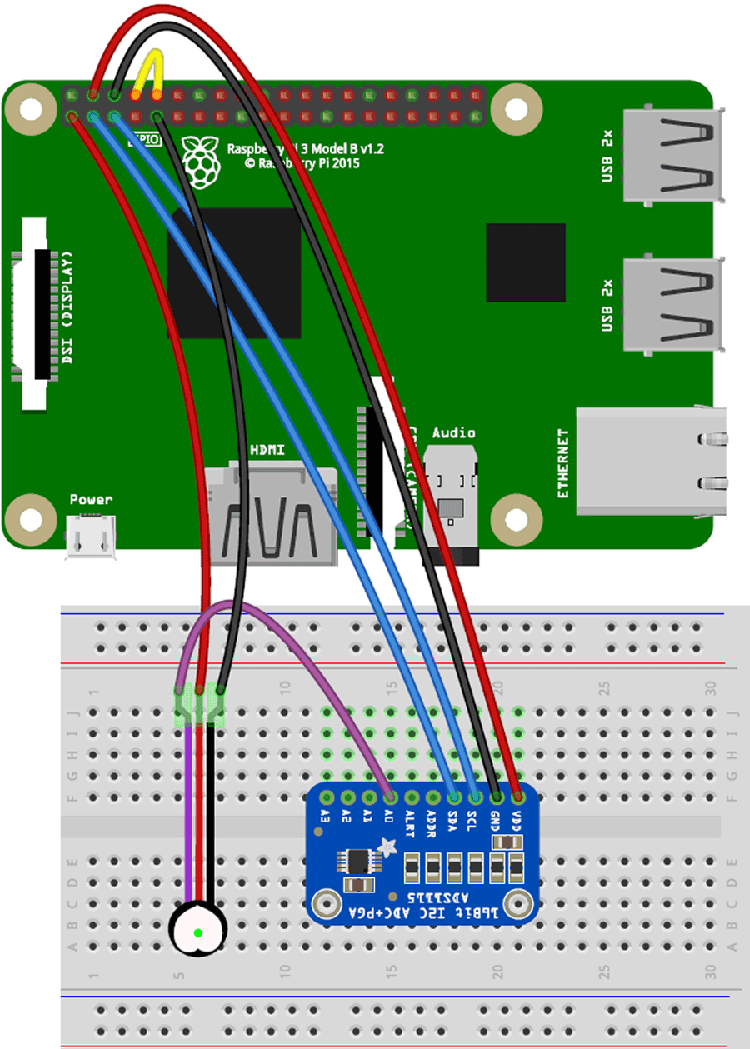
Remote IoT monitoring using SSH represents a significant leap forward in device management. This technology enables users to access and control IoT devices across networks without compromising security. For instance, consider Hassan Tariq, an electrical engineer based in Birmingham Gardens, New South Wales, Australia. With expertise in PLC, HMI, SCADA, and LV design, he has explored various applications of IoT systems. One notable project involved configuring a Raspberry Pi to operate a video camera and manage door locks via relay controls. Such projects highlight the versatility of combining SSH with IoT hardware, offering dynamic solutions tailored to specific needs.
| Personal Information | Details |
|---|---|
| Name | Hassan Tariq |
| Location | Birmingham Gardens, New South Wales, Australia |
| Professional Skills | PLC | HMI | SCADA | LV Design |
| Education | COMSATS Institute of Information and Technology |
| Career Focus | Electrical Engineering; IoT Systems Integration |
| LinkedIn Profile | View Profile |
Securely connecting remote IoT devices through SSH on platforms such as Raspberry Pi offers numerous advantages. By utilizing SSH IoT Anywhere, individuals and organizations gain the ability to remotely access and manage their devices while ensuring sensitive data remains protected. For example, integrating AWS services into a Raspberry Pi setup allows users to create secure Virtual Private Clouds (VPCs), further enhancing the reliability of their IoT infrastructure. This approach proves particularly valuable when deploying IoT solutions across geographically dispersed locations.
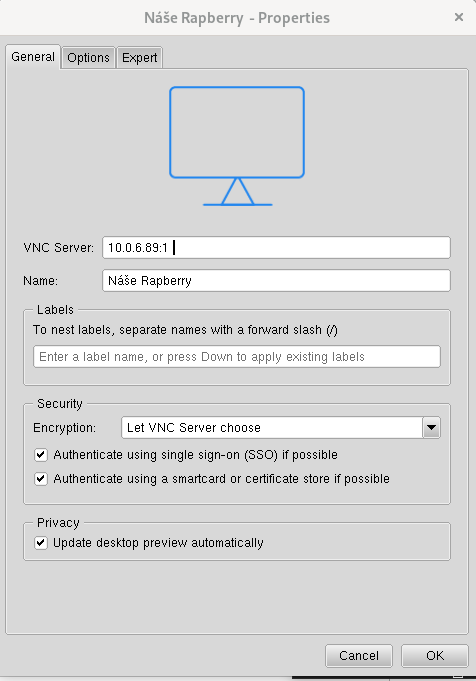
Downloading and implementing SSH IoT software involves several straightforward steps. First, ensure your Raspberry Pi runs a compatible operating system, such as Ubuntu. Next, configure the necessary network settings and establish secure credentials for authentication purposes. Once these prerequisites are met, downloading the SSH IoT client becomes a simple process. Many resources provide comprehensive guides to assist users throughout this implementation journey. These tutorials often include detailed instructions accompanied by visual aids, making them accessible even to beginners unfamiliar with advanced networking concepts.
Accessing IoT devices over the internet via SSH introduces additional layers of complexity but remains feasible with proper planning. Key considerations include firewall configurations, port forwarding rules, and public key authentication methods. Implementing these measures ensures unauthorized access attempts are thwarted while maintaining legitimate connectivity between authorized parties. Furthermore, leveraging cloud-based platforms like AWS simplifies the deployment process by abstracting much of the underlying technical detail associated with traditional server setups.
Mastering RemoteIoT Monitoring with SSH on Raspberry Pi empowers users to harness the full potential of IoT ecosystems. Through this methodology, individuals gain the capability to monitor, control, and troubleshoot their Raspberry Pi systems regardless of physical proximity. As IoT adoption continues its upward trajectory, familiarity with such techniques will undoubtedly prove advantageous for both personal projects and professional endeavors alike. Consider scenarios ranging from home automation systems to industrial automation processes—all benefit immensely from robust remote monitoring capabilities enabled by SSH integration.
The importance of securing remote connections cannot be overstated, especially within the context of IoT deployments. Ssh remoteiot functionality provides precisely this assurance when applied correctly to Raspberry Pi environments. Unlike alternative approaches that may expose vulnerabilities due to improper configuration practices, adopting best practices outlined within official documentation minimizes risks significantly. Additionally, eliminating reliance upon third-party intermediaries reduces exposure points susceptible to malicious exploitation.
As we delve deeper into practical examples illustrating effective utilization strategies, one recurring theme emerges consistently: preparation forms the cornerstone of success. Before embarking on any endeavor involving remote IoT monitoring using SSH, thorough research must precede execution phases. Understanding fundamental principles governing encryption protocols, authentication mechanisms, and authorization frameworks equips practitioners adequately for tackling challenges encountered during real-world implementations.
Take, for instance, a hypothetical scenario wherein multiple Raspberry Pi units serve as environmental sensors distributed across expansive agricultural fields. Each unit collects vital metrics concerning soil moisture levels, ambient temperature variations, humidity readings, etc., transmitting collected information back to centralized repositories for analysis. Enabling SSH-based remote access facilitates maintenance operations performed off-site whenever required, thereby reducing downtime attributed to manual intervention requirements.
In another illustrative case study, imagine a manufacturing facility employing IoT-enabled machinery equipped with embedded Raspberry Pi modules responsible for executing repetitive tasks autonomously under predefined conditions. Supervisors stationed elsewhere could leverage SSH connections to verify operational statuses periodically, identify anomalies promptly, initiate corrective actions swiftly, and document findings systematically—all without physically visiting premises themselves.
Moreover, educational institutions frequently incorporate similar technologies into curricula designed to impart hands-on experience regarding contemporary technological advancements impacting industry standards worldwide. Students participating in such programs develop invaluable skills transferable directly into workforce settings upon graduation.
From an economic perspective, embracing SSH-driven remote IoT monitoring translates into cost savings realized through enhanced efficiency gains achieved across diverse sectors spanning residential, commercial, and industrial domains alike. Reduced travel expenses incurred during routine inspections represent just one facet contributing positively toward overall budgetary optimization efforts undertaken by businesses seeking competitive advantages amidst increasingly crowded marketplaces characterized by rapid technological evolution cycles.
However, it is crucial to acknowledge certain limitations inherent within current implementations warranting attention moving forward. Latency issues occasionally arise depending upon prevailing network conditions affecting communication latencies negatively impacting responsiveness thresholds deemed acceptable under varying circumstances. Addressing these concerns necessitates ongoing refinement initiatives aimed at improving algorithmic efficiencies driving core functionalities powering modern-day SSH architectures supporting IoT applications.
Furthermore, addressing scalability constraints presents another challenge requiring innovative thinking beyond conventional paradigms traditionally employed thus far. Scaling horizontally requires careful consideration regarding resource allocation patterns balancing trade-offs between performance metrics versus monetary expenditures invested upfront establishing foundational infrastructures capable sustaining projected growth trajectories anticipated long term horizons considered relevant stakeholders evaluating strategic investment opportunities aligned organizational objectives pursued collaboratively amongst partners sharing common goals pursuit mutual benefits derived successful collaboration ventures embarked jointly.
Looking ahead, emerging trends suggest increasing convergence occurring between artificial intelligence (AI), machine learning (ML), and IoT ecosystems facilitated largely thanks advancements made possible integrating SSH methodologies enabling seamless interoperability amongst disparate components comprising holistic digital transformation initiatives undertaken enterprises striving remain relevant fast-paced global economy characterized unprecedented levels innovation disrupting established norms challenging status quo forcing adaptation survival thrive future landscapes envisioned thought leaders shaping destinies generations yet unborn.
In conclusion, mastering remote IoT monitoring using SSH represents more than merely acquiring technical proficiency; rather, it embodies commitment lifelong learning continuous improvement embracing change courageously navigating uncharted territories unlocking doors leading brighter tomorrows filled endless possibilities limited solely imaginations daring dreamers willing challenge boundaries explore unknown frontiers chart courses destiny ultimately determining legacies leave behind posterity remember fondly years henceforth reflect accomplishments achieved overcoming obstacles encountered along journeys traveled together united purpose shared vision brighter tomorrow awaits those brave enough seize moment embrace opportunity fully realize potentials latent within waiting unleashed boundless creativity fueling engines progress drive humanity forward ever onward upward towards greatness envisioned founders laid foundations built lasting monuments enduring test time standing testament achievements attained perseverance determination unwavering belief brighter future possible working hand hand achieving common good all mankind.