How can one effectively manage and monitor IoT devices remotely? A bold statement supporting this inquiry is that mastering SSH for Raspberry Pi not only enhances security but also empowers users to control operations seamlessly. In today's interconnected world, the ability to manage Internet of Things (IoT) devices from a distance has become indispensable. This skill set allows individuals like Hassan Tariq, an Electrical Engineer specializing in PLC, HMI, SCADA, and LV Design based in Birmingham Gardens, New South Wales, Australia, to leverage technology for efficient operation management.
Hassan Tariq exemplifies the modern engineer adept at integrating advanced technologies into everyday applications. With expertise in Raspberry Pi operations, he controls video cameras for capturing data and automates processes such as unlocking doors via relay systems. His proficiency extends beyond technical skills; he thrives both independently and within team environments, seeking dynamic opportunities to grow professionally. As part of the COMSATS Institute of Information Technology alumni network, Hassan maintains active connections on LinkedIn where his profile showcases over 448 professional contacts. Such networking highlights his commitment to evolving as an ambitious and goal-oriented individual.
| Name | Hassan Tariq |
|---|---|
| Location | Birmingham Gardens, New South Wales, Australia |
| Education | COMSATS Institute of Information and Technology |
| Professional Network | LinkedIn Profile |
| Specialization | Electrical Engineering - PLC | HMI | SCADA | LV Design |
| Skills | Raspberry Pi Operations, SSH Configuration, Remote IoT Monitoring |
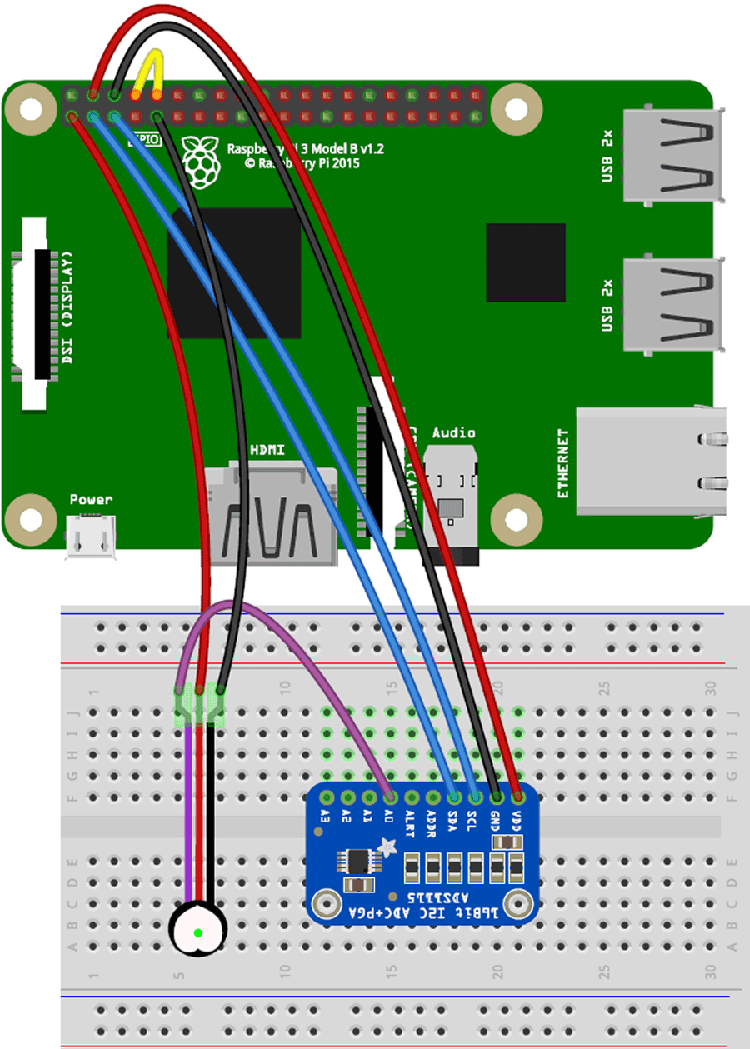
Understanding SSH for remote access represents a critical component of managing IoT devices effectively. Utilizing Raspberry Pi alongside Ubuntu operating system provides robust tools necessary for preparing systems capable of handling secure communications. By downloading SSH onto Raspberry Pi, configuring it appropriately ensures encrypted communication channels between connected devices. This setup facilitates reliable interaction with hardware components while maintaining high levels of cybersecurity.
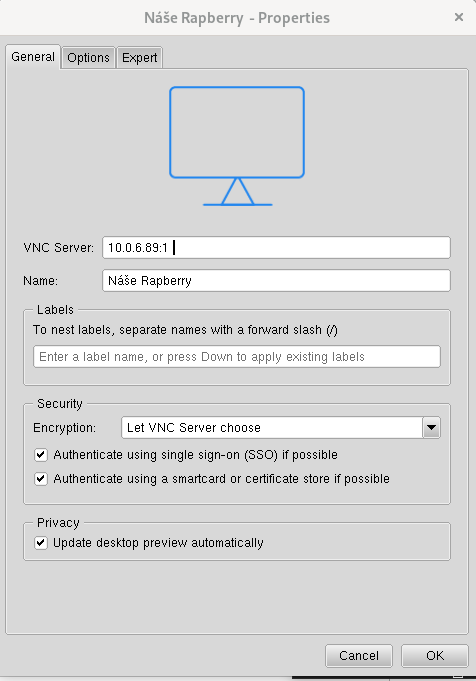
As the Internet of Things continues expanding globally, so does the demand for secure methods enabling remote management capabilities without compromising privacy or functionality. Integrating platforms like RemoteIoT simplifies configuration processes involved in setting up SSH access across various networks including those behind firewalls or NAT routers. Users gain flexibility accessing their devices securely regardless of geographical location constraints.
The comprehensive guide towards mastering SSH involves understanding fundamental principles underlying its operation before delving deeper into practical implementations tailored specifically toward IoT applications utilizing Raspberry Pi technology. Key aspects include learning about encryption protocols employed during transmission sessions along with best practices ensuring optimal performance under diverse environmental conditions.
For instance, when attempting to remotely access a Raspberry Pi located behind complex network architectures incorporating multiple layers of protection mechanisms such as firewalls or NAT routers, specific steps must be followed meticulously. Initiating connection ports by clicking 'Connect Port' options presented through interfaces provided by services associated with RemoteIoT yields unique hostnames accompanied by corresponding port numbers essential for establishing successful connections.
This innovative approach combining Secure Shell functionalities with versatile single-board computers opens new avenues for engineers worldwide aiming to enhance operational efficiencies within their respective fields. Whether monitoring industrial automation setups or personal home automation projects, harnessing these cutting-edge technological advancements equips professionals like Hassan Tariq with invaluable resources necessary to thrive amidst rapidly changing industry landscapes driven by continuous innovation cycles.
Incorporating SSH keys further fortifies security measures surrounding remote interactions involving sensitive information exchanges conducted over public internet infrastructures susceptible to unauthorized intrusions attempts. Establishing trust relationships between authorized parties prior initiating session handshakes guarantees authenticity thereby reducing risks associated malicious activities targeting unprotected endpoints exposed online environments.
Ultimately, embracing comprehensive strategies encompassing theoretical knowledge acquisition coupled hands-on experience implementing real-world solutions empowers aspiring technologists around globe achieve desired outcomes aligning closely with organizational objectives fostering growth sustainable development initiatives spanning multitude sectors relying heavily upon interconnected digital ecosystems thriving present era characterized unprecedented connectivity levels ever witnessed human history thus far.